The Real Problem
Active Directory delegations are one of the most overlooked security risks in enterprise environments. Most organizations have no visibility into what delegations exist, who has them, or when they change.
Many AD environments are 20+ years old with dozens of administrators over that time - each with different delegation approaches and business needs. Decades of accumulated delegations exist without proper documentation. Different admins granted different permissions for various projects and service accounts that may no longer exist.
Here's the reality: Many companies don't have dedicated IAM teams or even a single person focused on identity management. Adding another standalone tool just creates more overhead you don't have time to manage.
Many companies are focusing on cloud-only security and Entra ID while neglecting on-premises AD basics. Yes, you have Defender for Identity and Defender for Servers, but these don't replace fundamental delegation monitoring. If you can't remember the last time you reviewed AD delegations, it's time to address that gap.
- No automated daily delegation inventory across entire AD forest
- No change detection for new, modified, or removed delegations
- No integration with Log Analytics or Sentinel for security correlation
- No historical trend analysis or baseline establishment
The Solution: Use your existing Sentinel and Log Analytics tools for AD delegation monitoring. Same KQL queries, same dashboards, same alerting - just extended to cover delegation data from your domain controllers. Centralize all your security monitoring instead of managing separate tools.
Live Delegation Data in Sentinel
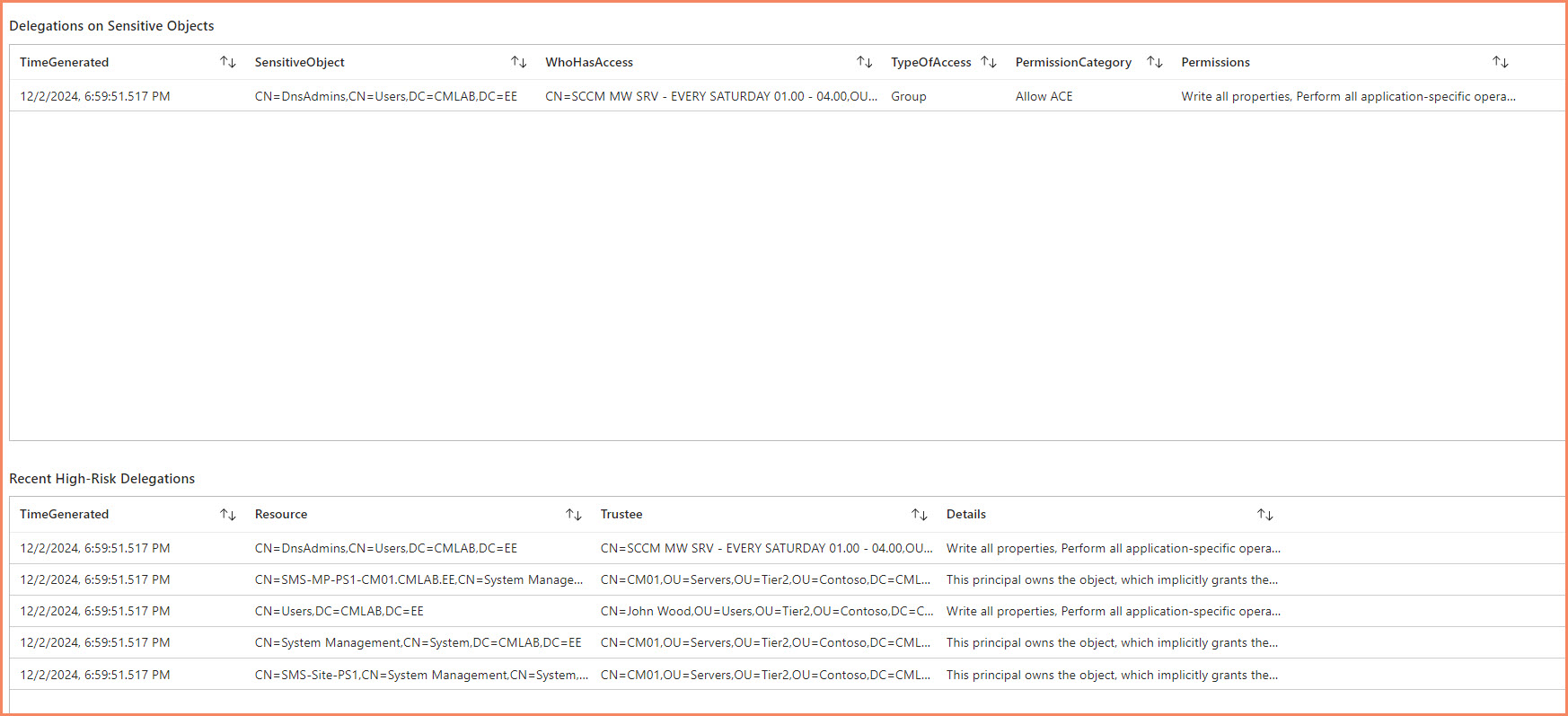
Why Standalone Tools Don't Work
If you've been working with Active Directory, you know it requires extensive scripting and monitoring. While many security experts recommend "just remove Active Directory," in most enterprise environments that's not realistic - legacy applications, business processes, and technical dependencies make AD removal a multi-year project at best.
AD delegations create privileged access that bypasses normal group membership controls. Service accounts and user accounts can receive delegation permissions that never appear in standard group membership reports or most monitoring tools.
There are excellent standalone tools for AD security analysis:
- PingCastle - Comprehensive AD security assessment and risk analysis
- Purple Knight - AD security posture assessment and hardening guidance
- BloodHound - Attack path mapping and privilege escalation analysis
- ADeleg - AD delegation inventory and security descriptor analysis
These tools are valuable for security assessments and understanding attack paths. For comprehensive AD security knowledge, also check out the AD Attack Defense repository which covers both attack techniques and defensive strategies.
The challenge: these tools require separate management, licensing, and reporting workflows. If you already use Sentinel and Log Analytics, you want delegation monitoring integrated with your existing infrastructure.
- No Change Tracking: New delegations appear without notification or logging
- No Audit Trail: You discover changes during incidents, not when they happen
- Manual Scaling Limits: Clicking through thousands of OUs doesn't scale
- Tool Fragmentation: Delegation data exists outside your SIEM
Real World Impact: Administrators grant broader permissions than required for quick fixes. Temporary project access becomes permanent. Help desk staff receive excessive permissions for convenience. Delegation scope exceeds actual business requirements. Over-privileged delegations accumulate over years without review across all account types.
Technical Solution Approach
Automated Daily Scanning
PowerShell automation runs scheduled tasks on domain controllers to scan entire AD forest for delegation permissions. Captures explicit permissions, inherited access, and service account rights without manual intervention.
Change Detection System
Daily comparison between scans identifies new, modified, and removed delegations. Maintains audit trail showing exactly what changed and when, with 24-hour detection window for delegation changes.
SIEM Integration
Query delegation data with same KQL queries you use for other security data. Azure Arc managed identity handles authentication without storing credentials.
Security Correlation Capabilities
Join delegation data with Windows Security Events, authentication logs, and privilege escalation events. Detect patterns like new delegations correlating with recent group membership changes or security incidents.
Data Flow Architecture
The solution bridges the gap between on-premises AD delegation data and your cloud security tools. PowerShell automation extracts delegation information from AD security descriptors and uploads structured data to your existing Log Analytics workspace.
Daily Process: Scheduled PowerShell scripts scan AD forest for delegation permissions, compare results with previous day's data, and upload both complete inventory and change deltas to separate data streams in Log Analytics.
No Infrastructure Changes: Uses existing domain controllers and Azure subscriptions. No new servers, agents, or third-party tools required.
Sentinel Integration
Delegation data flows into your existing Sentinel workspace through custom Log Analytics tables. Two separate data streams provide both complete delegation inventory and focused change tracking without requiring service principals or stored credentials.
- Complete Inventory - Daily delegation baseline for trend analysis
- Change Events - New, modified, and removed delegations for alerting
Security Correlation
Query delegation data alongside Windows Security Events, authentication logs, and privilege escalation events. Join delegation changes with group membership modifications to detect privilege escalation patterns.
Investigation Capabilities
Filter by delegation type, trustee pattern, or time range to investigate specific security scenarios. Correlate delegation changes with security incidents to understand attack scope and persistence mechanisms.
Working Solution Screenshots
KQL Query Interface
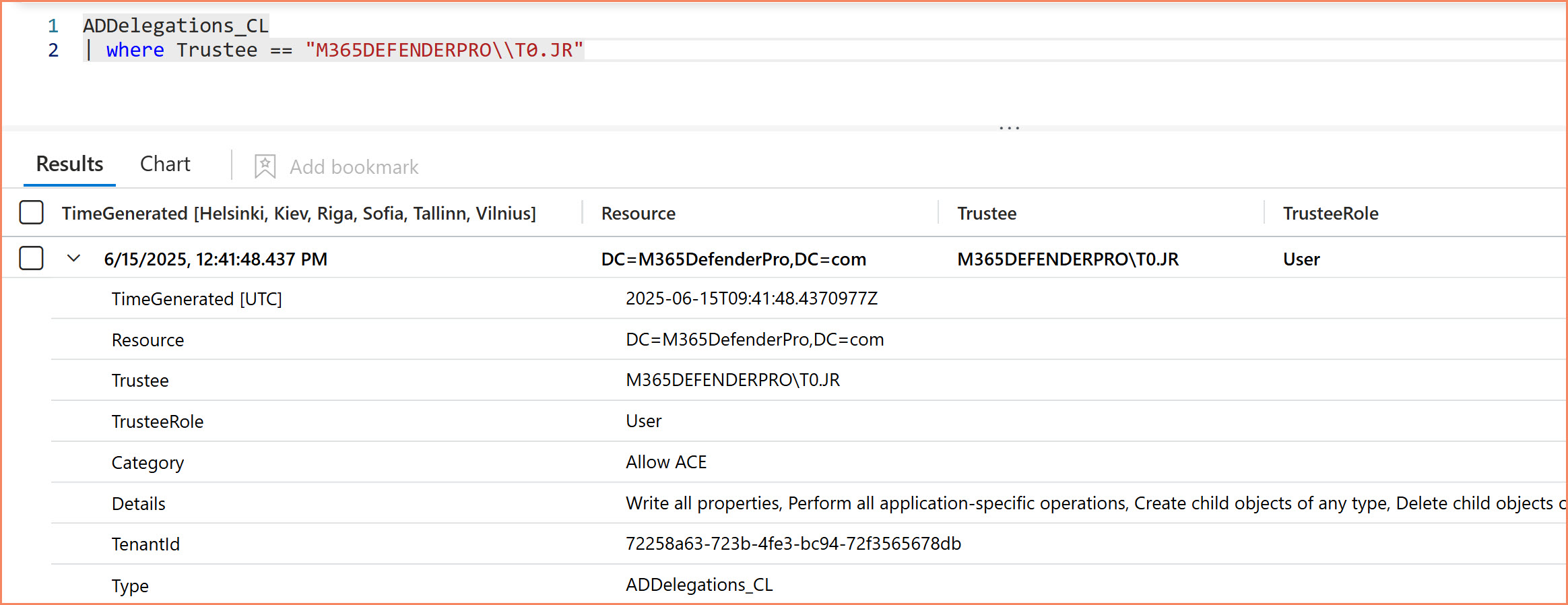
What the screenshots show: Delegation data appears in standard Sentinel interface alongside other security data. Change tracking provides timestamps and comparison data. Query interface works with same KQL syntax used for other Sentinel data sources.
Technical Prerequisites & Complexity
To implement this solution it is recommended to have Azure admin access, PowerShell experience, and domain admin permissions. The setup uses several Azure resources and PowerShell automation on your domain controllers.
- Azure subscription with Log Analytics workspace and Sentinel
- Domain Controller with Azure Arc agent installed
- Domain Administrator permissions for AD security descriptor access
- PowerShell scripting and Azure Data Collection Rules experience
If you don't have these infrastructure elements in place yet, you can set them up first. The implementation guide walks you through establishing the Azure environment and Arc agent deployment before implementing the delegation monitoring.
Skills Required: Azure administration, PowerShell automation, Active Directory security, Data Collection Rules configuration. The step-by-step guide helps you understand each component and learn the implementation process.
Complete Implementation Package
Everything needed to implement AD delegation monitoring from setup to production. PowerShell automation, Azure configuration files, Sentinel workbooks, and step-by-step implementation guides.
PowerShell Automation Suite
Production-ready automation including AD delegation analysis, change detection logic, Azure Arc integration, and scheduled task configuration. 500+ lines of tested PowerShell code ready for enterprise deployment.
Azure Infrastructure Setup
Complete Azure resource configuration including Log Analytics workspace setup, Data Collection Endpoints, custom table schemas, and managed identity configuration. Infrastructure-as-code approach for consistent deployment.
Sentinel Integration Components
Pre-built workbook with delegation analysis dashboards and investigation query library. Import directly into existing Sentinel workspace.
Implementation Documentation
Step-by-step guide covering Azure resource creation, script deployment, testing procedures, and troubleshooting. Includes configuration examples for different environment sizes and security requirements.
Validation & Testing Framework
Testing scripts to validate implementation, verify data flows, and confirm delegation monitoring accuracy before production deployment. Includes sample test cases and expected results.

