Introduction
Azure Arc servers get deployed, but tracking which ones are actually protected by Microsoft Defender for Endpoint becomes a manual nightmare. You have hundreds of Arc-enabled servers across subscriptions, but no visibility into security coverage gaps until an incident happens.
This automated integration solution discovers all Azure Arc servers, cross-references them with Microsoft Defender for Endpoint enrollment, and applies security tags directly in the Azure portal. Know instantly which servers are protected, their risk scores, and when they last checked in.
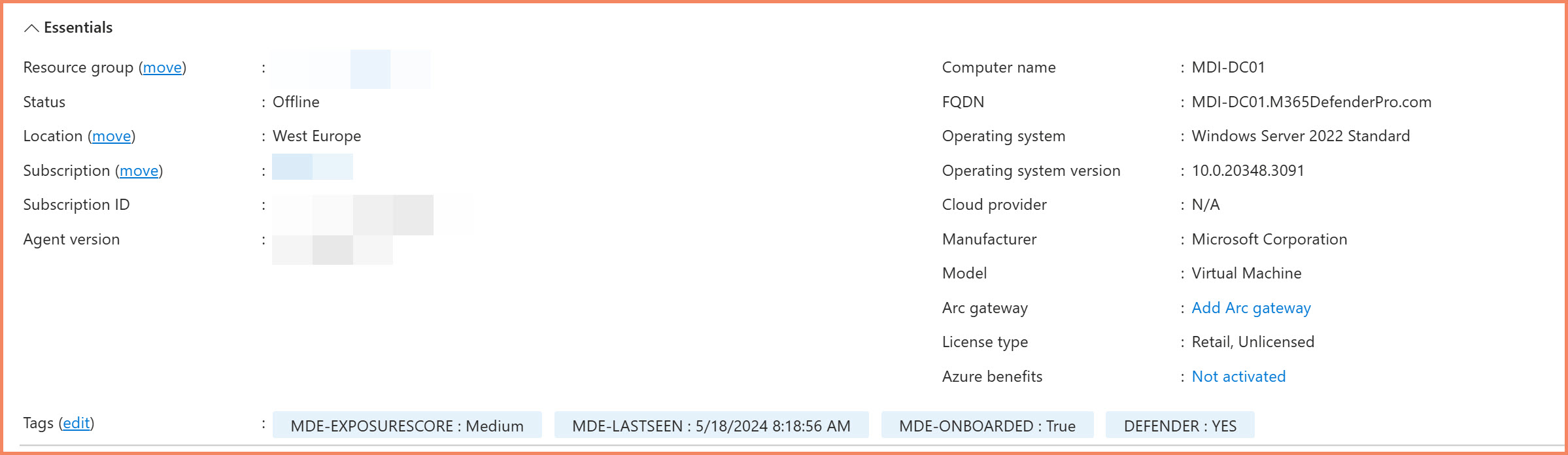
Automated security tags applied to Azure Arc servers showing MDE enrollment status, risk scores, and last seen timestamps
The Visibility Problem
Arc server deployments scale fast, but security enrollment tracking doesn't keep up:
- Coverage gaps - Arc servers deployed without MDE protection
- Manual checking - No automated way to verify MDE enrollment status
- No governance - Can't use Azure Policy without proper security tags
- Risk blindness - Don't know which servers have high exposure levels
- Incident delays - Only discover unprotected servers during security events
🚀 Get Instant Access to This Solution
Join the membership platform and download this ready-to-run solution today
MVP-Built Solutions • Production-Ready • Complete Documentation
Solution Overview
This Azure Arc & MDE integration solution uses Azure Resource Graph to discover all Arc-enabled servers, validates each one against Microsoft Defender for Endpoint APIs, and automatically tags resources with security status information.
Technology Integration
- Azure Automation - PowerShell runbook with managed identity authentication
- Azure Resource Graph - Fast cross-subscription Arc server discovery with pagination
- Microsoft Defender API - Real-time enrollment validation and security metrics
- Azure RBAC - Secure permissions for resource discovery and tagging
The solution runs on schedule, discovers all Azure Arc servers across your tenant, validates MDE enrollment status, and applies detailed security tags for governance and policy enforcement.
Architecture & Automation Flow
The security validation follows a four-step automated process:
- Discovery Phase - Azure Resource Graph queries all Arc servers with pagination support
- Enrollment Validation - Each server cross-referenced against Microsoft Defender for Endpoint
- Security Assessment - Risk scores, exposure levels, and last seen timestamps retrieved
- Tag Application - Arc resources automatically tagged with comprehensive security metadata
Key Features
🔍 Arc Server Discovery
Automatically discovers all Azure Arc-enabled servers across subscriptions using Azure Resource Graph with pagination support for enterprise environments.
🛡️ MDE Enrollment Validation
Cross-references each Arc server against Microsoft Defender for Endpoint to verify protection status and retrieve security metrics.
🏷️ Automated Security Tagging
Applies MDE enrollment status, risk scores, exposure levels, and last seen timestamps directly to Arc resources as Azure tags.
📊 Security Metrics Integration
Captures comprehensive security data including device risk scores, exposure levels, and last communication timestamps for governance visibility.
Technical Requirements
Azure Infrastructure
- Azure Automation Account with managed identity enabled
- Azure Arc-enabled servers to monitor
- Microsoft Defender for Endpoint licensing and enrollment
- PowerShell 7 runtime environment in Automation Account
What You Get
Complete solution package ready for deployment in your environment:
- PowerShell automation script for Arc server discovery and MDE validation
- Azure Automation runbook with scheduled execution capabilities
- Microsoft Defender API integration with comprehensive error handling
- Step-by-step deployment guide with RBAC configuration
- Scalability guidance for large environments (1000+ servers)
Complete Implementation Guide
The full Azure Arc & MDE Integration solution includes:
- Complete Azure Automation Account setup with managed identity configuration
- Microsoft Defender API permissions and authentication setup
- PowerShell runbook script with MDE enrollment validation
- Azure Resource Graph query optimization for large environments
- Automation scheduling configuration and monitoring setup
- Security tag schema and Azure Policy integration examples
- Troubleshooting guide and common error resolution steps

