The Real Problem with Entra ID Logs
If you've been working with Entra ID logs, you know it's not the easiest thing to deal with. You open the Azure Portal or Entra portal, select a user, and list their sign-in activities. But you quickly discover it's painfully slow and getting simple answers is frustrating - like how many locations did they use, what's the time gap between different locations, how many devices, etc.
Sign-in logs are split into two groups: interactive and non-interactive. Interactive logs are manageable because the count stays low. Non-interactive logs are a different story - the volume is massive and analyzing them manually becomes nearly impossible.
When you get that urgent call and someone says "I need this data and that analysis," the Entra portal becomes your worst enemy. You might also be in an environment with no SIEM or Sentinel at all. Your only real option? Graph API to extract the sign-in data directly.
- Slow Performance: Portal crawls to a halt with large datasets
- No Quick Answers: Simple questions like "how many devices?" require tedious manual counting
- Data Correlation Hell: Interactive and non-interactive logs exist in separate silos
- No SIEM Available: Many environments lack Sentinel or other SIEM tools
- Export Nightmare: Portal exports are basic CSV files that need hours of manual processing
🚀 Get Instant Access to This Solution
Join the membership platform and download this ready-to-run solution today
MVP-Built Solutions • Production-Ready • Complete Documentation
When Legal Calls: "We need all sign-in activity for user X between these dates, including device information, locations, and impossible travel analysis." Good luck doing that manually through the portal - you'll be there for days.
Graph API Data Extraction Approach
Direct Graph API Integration
PowerShell automation connects directly to Microsoft Graph API auditLogs/signIns endpoint to extract comprehensive sign-in data. Retrieves both interactive and non-interactive authentication events with full metadata preservation.
Multi-Dimensional Data Processing
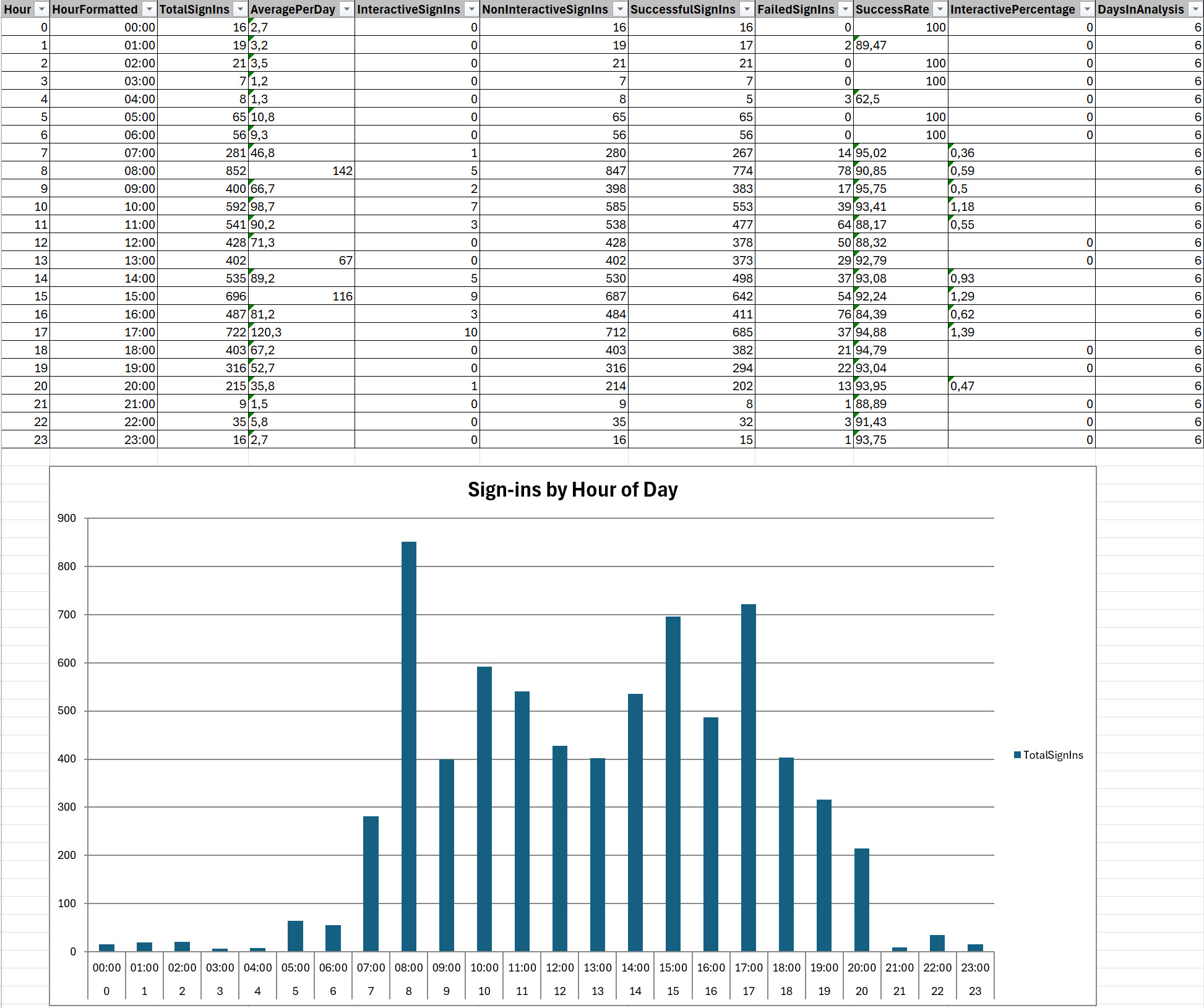
Single data extraction generates 16 specialized CSV files analyzing the same sign-in events from different perspectives: timeline, geographic, device, application, mobile classification, and behavioral analysis.
Forensic Data Structure
Maintains original timestamps, correlation IDs, and metadata for audit trail preservation. Structured outputs support database import, Excel analysis, and legal discovery requirements.
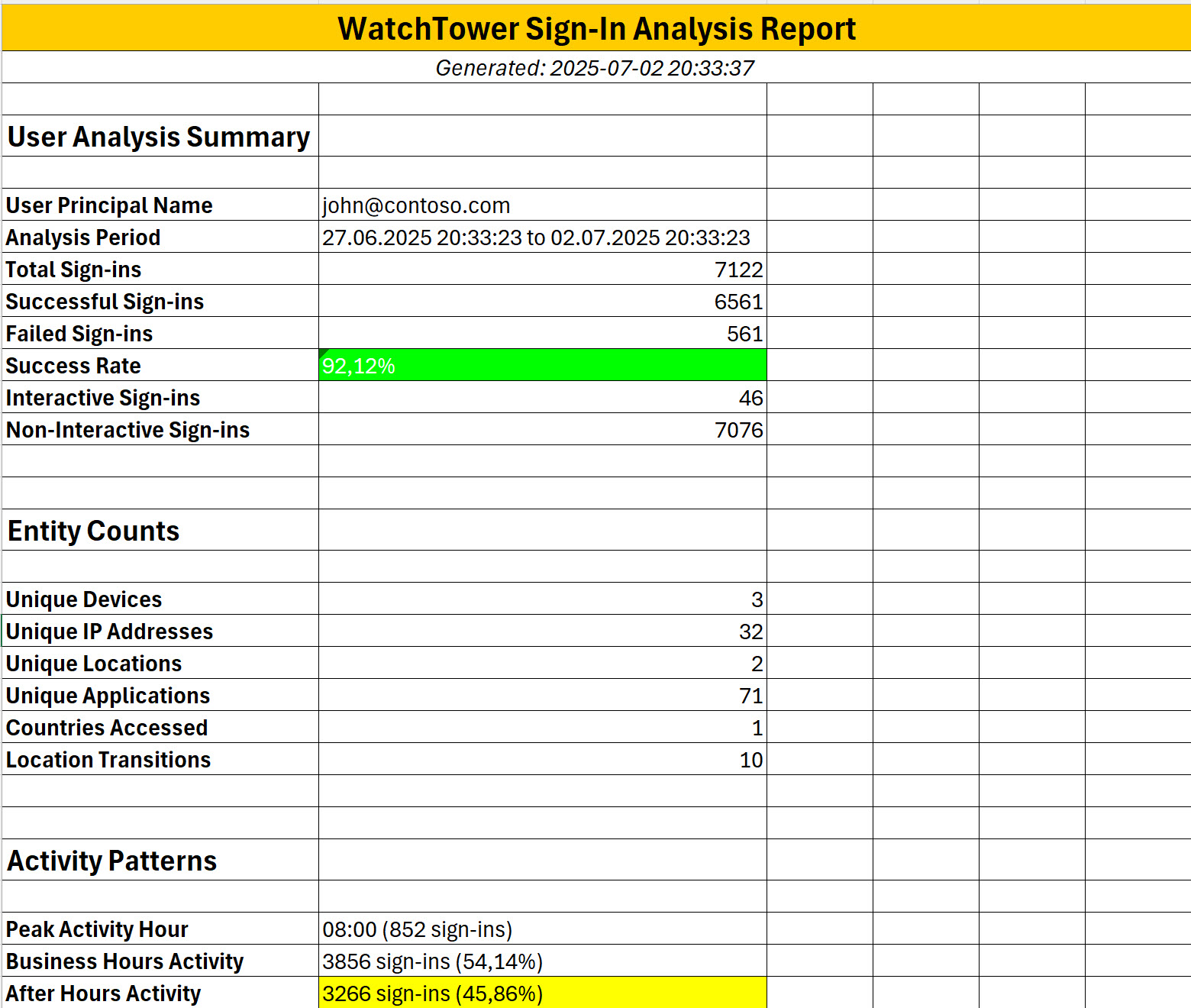
What Exactly You Get Out
Instead of clicking around the portal for hours, you run one PowerShell command and get structured data exported into multiple CSV files. Each CSV file analyzes the same sign-in data from different angles:
16 Specialized CSV Files
- Timeline.csv - Chronological events with timestamps, mobile detection, and correlation IDs
- Devices.csv - Device compliance, OS, browsers, usage patterns
- IPAddresses.csv - IP behavioral analysis, success rates, geographic correlation
- Locations.csv - Geographic access patterns with coordinates
- Applications.csv - Application access patterns and correlation analysis
- Browsers.csv - Browser usage and security analysis
- CountryAnalysis.csv - Country-level access patterns and anomalies
- LocationTransitions.csv - Travel patterns and impossible travel detection
- DeviceAnomalies.csv - Devices used from unusual locations
- SuspiciousPatterns.csv - Detected patterns requiring investigation
- HourlyPatterns.csv - 24-hour activity heatmap data
- DailyPatterns.csv - Weekly activity patterns with mobile breakdown
- DateBreakdown.csv - Daily calendar view with mobile/deviceless metrics
- BusinessHours.csv - Work vs after-hours analysis
- DevicelessSignIns.csv - Events without device identification (security-critical)
- Summary.csv - High-level statistics and metrics
JSON Data Preservation
Raw Graph API responses preserved in JSON format for audit trails. Three JSON files: raw logs, processed analysis, and full correlation data.
Combined Excel Dashboard
All CSV data combined into one Excel file with charts, factual metrics, and executive dashboard. Visual presentation suitable for legal discovery and compliance reporting.
PowerShell Automation
Production-ready PowerShell scripts that handle Graph API authentication, pagination, error management, and data processing. Just run the script and get your forensic data.
Prerequisites and Complexity
- Entra ID tenant with sign-in log retention
- Graph API permissions (AuditLog.Read.All, Directory.Read.All)
- PowerShell 7.x with Microsoft Graph PowerShell SDK
- Global Reader or Security Reader role minimum
Business Applications: Security incident response with detailed timelines. Legal discovery requests requiring structured user activity data. Compliance audits needing quantified access patterns. Risk assessments without dedicated forensic tool investments.

