Introduction
If you've been working with Windows LAPS (Local Administrator Password Solution) in your Active Directory environment, you know the challenge: Microsoft gives you the password management capability, but leaves you completely blind to who's accessing those passwords and when.
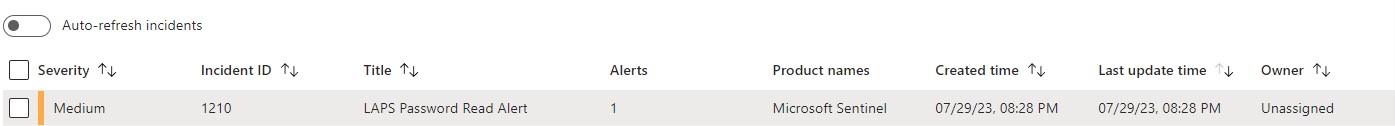
This monitoring solution fills that critical security gap by providing comprehensive tracking and auditing of Windows LAPS password access events through Microsoft Sentinel integration.
The LAPS Monitoring Challenge
Let's face it - most admins aren't going to manually sift through thousands of Event ID 4662 logs on domain controllers. Many environments don't even have the proper audit settings configured.
Microsoft gives you LAPS password management but provides zero monitoring tools. You literally don't know:
- Who's accessing LAPS passwords - No visibility into user access patterns
- How often passwords are retrieved - No frequency tracking or unusual access detection
- For which devices - No correlation between password access and target systems
- If attackers are mass-dumping passwords - No detection of bulk password extraction attempts
🚀 Get Instant Access to This Solution
Join the membership platform and download this ready-to-run solution today
MVP-Built Solutions • Production-Ready • Complete Documentation
Microsoft built LAPS but left monitoring as an exercise for the admin. This solution provides the missing piece: end-to-end visibility through tools you already have.
Solution Overview
This Windows LAPS monitoring solution transforms Event ID 4662 from your domain controllers into actionable security intelligence through Microsoft Sentinel.
Technology Integration
- Azure Monitor Agent - Collects security events from domain controllers
- Microsoft Sentinel - Processes and analyzes LAPS access events
- Custom KQL Queries - Filters and correlates LAPS password access
- Analytics Rules - Generates alerts based on access patterns
The solution monitors Windows LAPS password access across your entire Active Directory infrastructure, providing security teams with complete visibility into privileged access patterns.
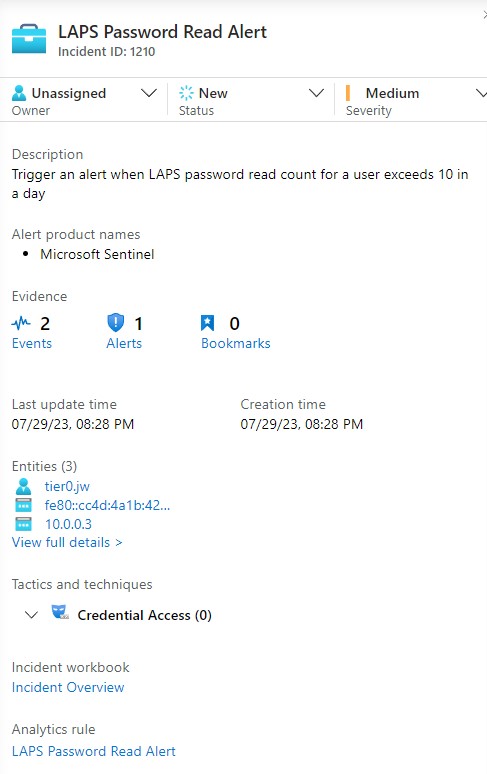
Architecture & Data Flow
The monitoring architecture follows a four-layer approach:
- Event Generation - Domain controllers generate Event ID 4662 when LAPS passwords are accessed
- Collection & Normalization - Azure Monitor Agent collects and processes security events
- Detection & Analysis - Sentinel analytics rules scan normalized logs for suspicious patterns
- Response & Alerting - Automated incident creation and notification workflows
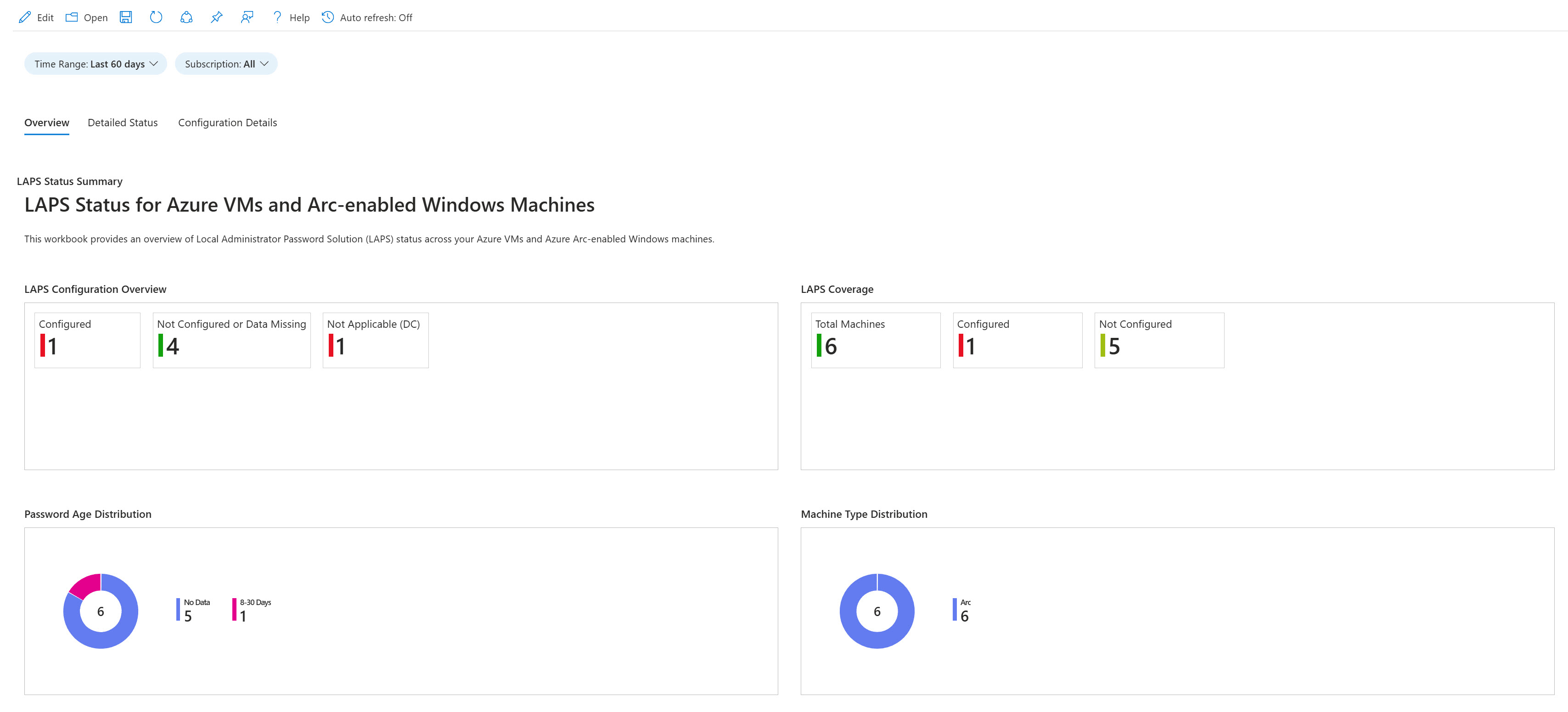
Key Features
🔍 LAPS Access Tracking
Monitor every Windows LAPS password access with detailed event correlation and user identification across your Active Directory environment.
📊 Activity Analysis
Track access frequency, identify patterns, and generate reports on LAPS password usage across all domain controllers and systems.
🚨 Automated Alerting
Custom analytics rules generate alerts for suspicious LAPS access patterns, unauthorized usage, and compliance violations.
📋 Compliance Reporting
Complete audit trails for regulatory compliance with detailed LAPS password access logs and user activity reports.
Technical Requirements
Active Directory Environment
- Windows Server domain controllers with LAPS deployed
- Directory Service Access auditing enabled
- Object-level auditing configured for LAPS attributes
Azure Infrastructure
- Active Azure subscription with appropriate permissions
- Microsoft Sentinel workspace configured
- Azure Monitor Agent deployment capability
- Azure Arc (if domain controllers are non-Azure)
Skills & Experience
- Windows LAPS administration experience
- Active Directory security configuration knowledge
- Basic Microsoft Sentinel familiarity
- PowerShell and KQL query experience helpful
Implementation Scope
The complete solution includes five major implementation phases:
- Environment Preparation - Configure Active Directory audit settings and validate LAPS deployment
- Agent Deployment - Install and configure Azure Monitor Agent on domain controllers
- Sentinel Configuration - Set up data collection rules and workspace integration
- Query Development - Implement custom KQL queries for LAPS event analysis
- Alerting Setup - Configure analytics rules and incident response workflows
Security Benefits
Threat Detection
Identify suspicious Windows LAPS password access patterns that could indicate:
- Unauthorized privilege escalation attempts
- Compromised service accounts accessing LAPS passwords
- Unusual access times or frequency patterns
- Cross-domain LAPS password access anomalies
Incident Response
Rapid identification and investigation capabilities for LAPS-related security events with complete audit trails and correlation data.
Compliance & Auditing
Meet regulatory requirements with comprehensive LAPS access documentation:
- Complete access logs with user identification
- Time-stamped audit trails for all LAPS password retrievals
- Correlation between LAPS access and subsequent system activities
- Automated compliance reporting capabilities
Complete Implementation Guide
The full Windows LAPS monitoring solution includes:
- Step-by-step Active Directory audit configuration guide
- Azure Monitor Agent deployment scripts and procedures
- Complete Microsoft Sentinel workspace setup
- Custom KQL queries for LAPS event analysis
- Analytics rules and alerting configuration
- Testing and validation procedures
- Troubleshooting and optimization guidance

